Blog | Securence - Part 2
Benefits of Securence Spam Filtering
Spam is most well-known for spreading viruses and scams to unwitting people across the internet, but it can actually cause plenty of problems for the modern business. This is why effective spam filtering, like Securence spam filtering, is an important part of running a successful business in the 21st century. Here are just a few reasons why spam filtering is important for not only keeping you safe from viruses, but also for helping your company be more effective and successful.
1. It Streamlines Inboxes
The average office worker receives roughly 121 emails per day, half of which are estimated to be spam. But even at 60 emails a day, it is easy to lose important communications to the sheer number that are coming in. This is one of the secret benefits of spam filtering that people do not know about: it simply streamlines your inbox. With less garbage coming into your inbox, you can actually go through your emails more effectively and stay in touch with those who matter.
Malware, viruses, and other forms of malicious attacks are heading to people’s email inboxes every day. Some of these can be easily weeded out by your internet provider’s own spam filters, but spam gets smarter every day. Smarter spam gets into more inboxes, which makes it more likely to be opened and more likely to cause harm. With spam filtering, you can stay on top of the many spam tactics that are being used today so you can ensure that your email inboxes stay free of harmful messages.
3. Keeps You Compliant
Many small and medium sized businesses are losing out on important clients today because their cybersecurity is not up to par. Spam filtering is a major part of any cybersecurity plan, and it helps you stay compliant with the wishes and demands of companies and agencies that are concerned about their information. Without proper spam filtering, you could unwittingly put spyware in your emails and break security protocols. The result could be a loss of business, reputation, and ultimately income.
4. It Saves You Money
Every day, someone falls prey to a phishing scam, a particular kind of spam-based scheme where someone thinks they are getting a legitimate email and ends up divulging credit card information. Sometimes it is a personal credit card, sometimes it is a company credit card. In both instances, the end result is losing valuable time and money to a scam.
Spam filtering is also incredibly affordable, making it a cheap but extremely effective way to keep yourself safe.
Your inboxes need to be effective tools for communication, not a place where anyone can get into and start hitting you with useless or dangerous emails. That is why spam filtering is such an important aspect of modern businesses. Rather than relying on outdated, free spam filtering services, choose Securence spam filtering. With up-to-the-minute security protocols, it can help your business communicate more effectively while keeping malware out of your inboxes, all for less than you may think.
Securence User Guide
Email Quarantine
Securence scans each of your emails to determine whether or not they are spam. Securence retains messages it determines to be spam in your personal Quarantine. Instead of allowing spam to be delivered to your inbox, Securence stores these messages securely for a period of 30 days. After which, they will be automatically deleted.
Spam Digest
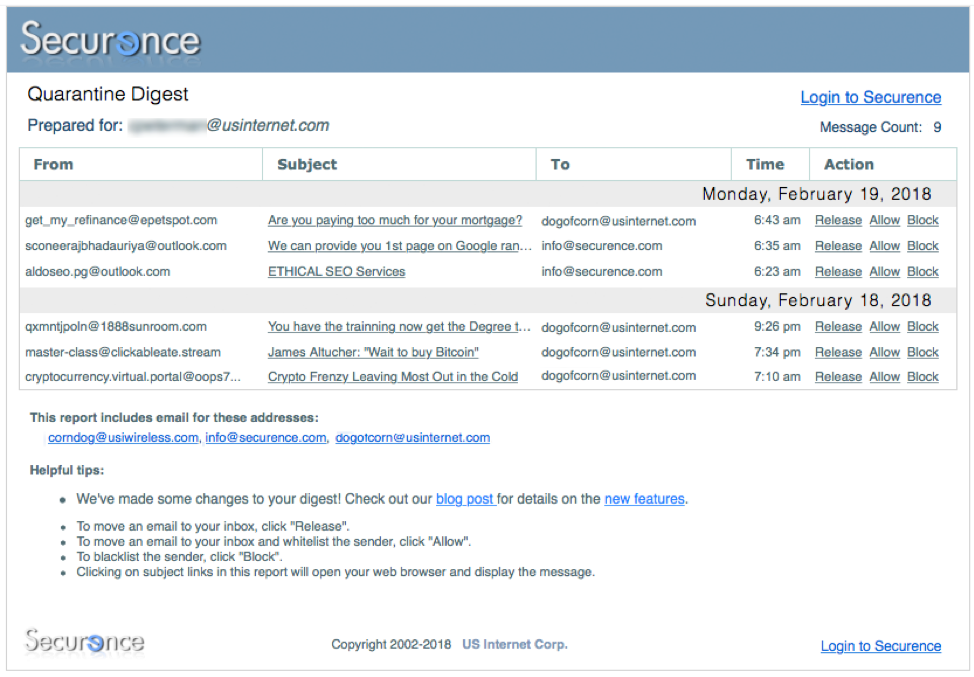
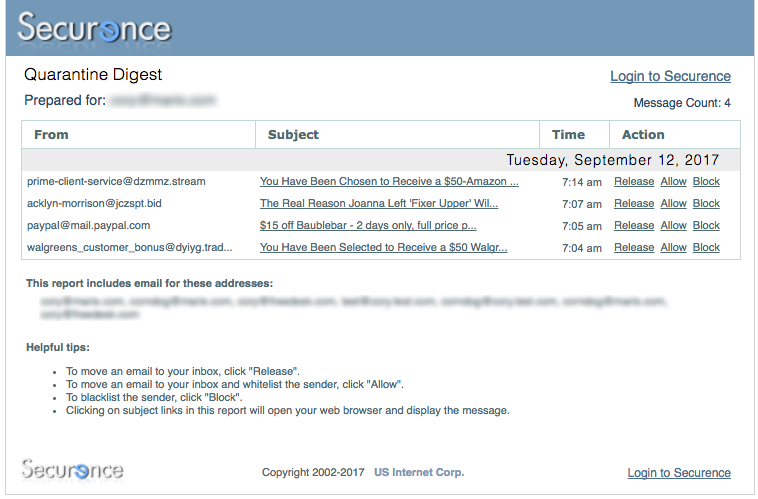
If your administrator has enabled the Spam Digest, you will receive a regular summary by email of the most recent messages quarantined for your address. This digest will be sent to you according to the schedule determined by your administrator. The following is an example of a typical digest:
For each quarantined message, the digest displays standard message attributes: sender address, subject, recipient address, date/time and available actions. To view a quarantined message, simply click on the subject of the message you wish to view and it will be displayed in your web browser. For each message, there are various actions that can be taken directly from the digest:
- If the message is spam, no action needs to be taken. It will be automatically deleted after 30 days.
- To move an email to your inbox, click “Release”.
- To move an email to your inbox and whitelist the sender, click “Allow”.
- To blacklist the sender, click “Block”.
When viewing a quarantined message in your web browser, additional actions may be accessible to you, such as “whitelisting” the sender. This will add the sender’s address to your list of trusted senders and prevent mail from them from being marked as spam.
Viewing your Quarantine online
Another way to view your quarantined messages is by logging in to the Quarantine interface through a web browser.
This allows you to browse all quarantined messages sent to your email address.
Either click the Login to Securence link at the bottom of your spam digest or
open a web browser and visit https://admin.securence.com/
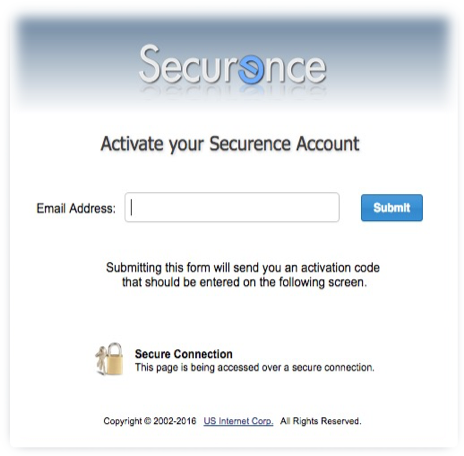
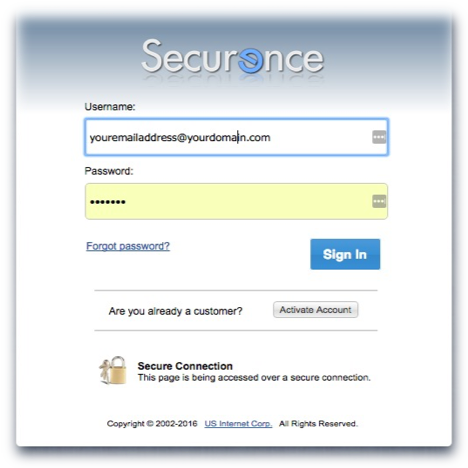
Activating your account
If this is the first time you are logging in and your administrator has not provided you with a password, you will need click the Activate Account button. You will be taken through a series of steps in order to confirm your identity and get started with Securence:
- Enter your email address.
- Securence will send an email to your address containing a confirmation code. Leave this window open.
- Check your inbox for a new email from Securence. (If you don’t receive an email, make sure to check your Junk mail folder)
- Return to your web browser, enter the confirmation code from the email into in the box as directed and click Confirm.
- Create a password.
- Click “Submit password and login”
You should now be able to view your Quarantine and/or manage your individual user settings in Securence.
Managing your quarantined messages
Here is an example of how the Quarantine interface appears upon logging in:
From here, you can search your Quarantine based on multiple criteria including sender address, recipient address, and subject. To view a message, simply double-click the row in the grid for the message you would like to view.
Additional options from within the Quarantine interface that may be available to you:
- Whitelist Sender. “Whitelisting” the sender pre-approves all emails originating from them for delivery to your inbox and prevents them from being marked spam.
- Release. This will release a message from the quarantine and deliver it to the originally intended recipient.
- Forward. You may forward a quarantined message to a different address.
- Delete. This will delete the message from your quarantine making it no longer visible or available for release.
If your outgoing mail is also filtered by Securence, you may view those quarantined messages separately by first clicking on the Outgoing tab at the top of the page.
You may also take action on multiple messages at one time. Select all applicable messages by checking the box in the left-hand column. Then click the desired action (e.g. Release, Forward) at the bottom of the window.
Reporting False Negatives
A false negative is an actual spam message that was not filtered out and sent along to your inbox. If you believe a message has been delivered to you that is spam, you may forward it to spam@securence.com. Submitting spam in this way helps to improve the mail filters in Securence.
Email Continuity
In the event of an email server outage, you can still access inbound email through your Continuity mailbox. To access your Continuity mailbox, go to https://webmail.securence.com and login using your regular email address and password.
If you have forgotten your password, click the Forgot password link and you will be able to create a new one. However, while your email server is down, since you cannot receive new messages, this procedure requires that you have either an alternate email address or mobile phone number configured in Securence. Securence will send a confirmation code using either of these alternate channels in order assist you in changing your password.
Continuity is an additional feature that may or may not be enabled for your domain. Consult your system administrator to confirm access to this powerful feature.
Four Reasons Why You Need Better Email Archiving
Email archiving, or the practice of safely storing the information in your company’s emails, is an important aspect of the modern business. Since our information, and the information of our clients, is paramount, you need an archiving system that is easy to use and ultra-secure. This is why Securence offers a variety of email archiving packages that ensure your emails are safe and easily searchable. Here are just a few reasons why people are making the switch to higher quality email archiving.
1. Making the Switch is Seamless
When you choose Securence for your email archiving, you are investing in a flexible archiving system. The email itself can be customized to work the way in which you are familiar, so you can hit the ground running without having to learn an entirely new system.
2. It’s Easy to Search
Securence’s email archiving not only protects and catalogues every email sent through your company, but it also features an easy-to-use search function to help you pinpoint the email correspondences that you need. You can search through multiple criteria, including by a date or a range of dates, by sender or recipient, by ID or IP address, attachment file name, subject line keywords, and the body text of attachments or the messages themselves. You can even search all incoming messages, outgoing messages, journaled messages, or any combination of the three. Performing these searches requires little more than checking a few boxes, in most instances, and the search results are instant. You can even save previous searches so you can easily locate messages that you’ve found previously.
 3. Your Emails Can Be Safer
3. Your Emails Can Be Safer
Every archiving package that we offer includes up-to-date encryption protocols in order to ensure that your email archive is safe and compliant with security protocols. The encryption systems that we use are considered the “gold standard” of email encryption, ensuring that your system is safer than it would be if it were left alone with one of the lower cost or free email providers. That means your emails will be safer while easier to find, all by switching to our archiving services.
4. Reliable Disaster Recovery
Some email archiving systems have weaknesses built into how they store emails, either without relying on redundant servers or by using non-dependable server providers. At Securence, we ensure that your email archive is securely stored on reputable servers, and that there are sufficient redundancies in place to ensure you will never lose a single email. The servers are updated in real time instead of every few minutes to ensure everything is up-to-the-second accurate. And in the event of a server issue, your emails will still be accessible.
High quality email archiving (http://www.securence.com/category/email-archiving/) offers a secure and easy-to-use way to store and search your entire database of emails. It can help you stay compliant with security protocols without slowing you down, and it offers you and your clients the peace of mind knowing that your emails are secure.
Securence™: Protection Against Zero Day Virus Attacks
What is a zero day virus?
A zero day virus, is, simply put, a new computer virus for which there is no defense. It is designed to exploit your system’s vulnerabilities, taking advantage of the fact that even the largest antivirus protection programs, like AVG™, Norton™, and McAfee®, have no ready solution.
Most antivirus programs use “signals” to search your computer for malicious codes, attachments, and viruses. But a zero day virus is like a stealth bomber. It flies “under the radar” and does not send off a known signal. Most programs develop a patch to fix the problem after the attack has occurred, but Securence™ has a better solution. We can stop a zero day virus before it does any damage to your private and sensitive data. Read on to learn how.
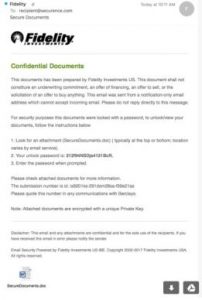 How Sneaky is a Zero Day Virus? Very!
How Sneaky is a Zero Day Virus? Very!
One of the most common ways to infect a computer is to create a malicious email attachment. Most of these email attachments look completely legitimate. For example, let’s say Fidelity Investments is your financial advisor, so you have their name, address and personal advisor’s details in your email contact list. If you get an email from Fidelity that looks like this:
would you hesitate before opening it? It’s from a name you trust. It’s on letterhead. There are no spelling mistakes. It contains information that looks familiar to you…and it’s a trap.
Securence put this Fidelity zero day virus to the test. Using Virus Total, an analytical tool that simultaneously harnesses the power of 57 antivirus scanners, we scanned the fake Fidelity document. The results were scary.
Out of 57 scanners, only four caught the virus. This virus fooled Malwarebytes, McAfee, AVG and even Microsoft – and this zero day virus was sent on Microsoft’s own exchange servers!
We ran this same file through our own Securence program; and it caught the virus. That’s because while many of the best antivirus software programs search for signals, Securence adds another layer of protection by also searching for patterns.
 Securence Protects Against Zero Day Viruses
Securence Protects Against Zero Day Viruses
We are not saying that other virus protections are inadequate. Some protection is better than none. However, zero day viruses are specifically designed to circumnavigate to the top names in antivirus protection, so for full protection, you need something more. That’s where Securence steps in.
As mentioned above, our leading enterprise email filtering system doesn’t just look at signals. It analyzes the patterns that zero day viruses use, and anticipates the signals and patterns that new zero day viruses may use in the future. Our program is designed to be proactive and agile so we can stay ahead of the hackers that want your private information. Our solutions cover you from every angle: inbound and outbound email filtering, first-in-class encryption, secure email archiving, email shadowing and much more.
You Deserve Protection Against Zero Day Viruses
You, your company and your clients deserve the best possible protection against zero day viruses. Our solutions are affordable, complete, and incredible agile. Rather than providing retroactive fixes once a zero day virus attacks, we focus our R&D on stopping zero day virus before they access your data. Only 7 percent of 57 top scanners caught the Fidelity virus, and we were one of them. For smart protection, call Securence today.
Securence = Lowest Cost Email Protection System
Email security protocols are always changing as hackers discover new ways to break into email accounts. That is why Securence offers a wide range of email protection services with every email security package. These services not only help keep your Office 365 email accounts safe; they can also help cut the clutter and keep you running in case of a server crash. Best of all: Securence will beat any competitor’s pricing so you can enjoy the best email security protection program available at an unbeatable price.
Here are the services you can expect when you choose Securence as your email security provider.
1. Lowest-Cost Inbound Filtering
One of the greatest threats to any email account is the mail that manages to show up in the inbox. It is likely that your Office 365 filters are strong by default, but hackers and malicious email scammers are always outpacing Microsoft’s security protocols. It is one of the most important reasons why companies need extra protection.
Inbound filtering will help eliminate external threats to your business’ email accounts. These can include phishing schemes, requests from foreign “princes,” and other emails that could potentially contain viruses or spyware.
2. Lowest-Cost Outbound Filtering
Just as inbound filtering protects your email accounts from certain external attacks, outbound emails can help contain the spread of these attacks. In the case where someone manages to download a malicious email, outbound filtering can help their email stop the spread.
3. Lowest-Cost Email Continuity
Almost every major tech company that offers email suffered server outages this year, including Amazon and Google. These outages can sometimes last a barely-perceived minute or a couple of days. In each instance, emails sent and received during those outages are lost and accounts are all but inaccessible. Email continuity services provide a backup email server that is constantly updated with every piece of mail sent. When the primary servers go down, these servers seamlessly take over. And when the primary servers go back up, they are automatically updated with all of the information sent during the outage.
4. Lower-Cost Email Encryption
Email encryption is an extra layer of security that helps ensure your emails are seen by the intended recipients and no one else. Without added encryption, sensitive information sent via email can be intercepted, including credit card information, personal details, and other data that should be away from prying eyes.
5. Lowest-Cost 10-Year or Unlimited Year Email Archiving
Finally, Securence offers email archiving services to ensure that your emails are always available. This program can help you stay compliant with federal regulations and your clients’ own security expectations, all while ensuring every email is at your fingertips.
Securence offers the most effective and lowest cost solution for safe-guarding your Office 365 email system. With a wide array of email filtering, protection, and continuity services built right into every package, you and your business can enjoy unprecedented email protection at the lowest cost available. Not only will Securence price match any competitor’s pricing, but they will also beat it so that you can have the protection you need at a price you can afford.
Protect Your Office 365 Users with Securence
Being one of the most popular email services on the planet, Microsoft’s Office 365 has also become the most popular target for cyber attacks. People are constantly targeting Microsoft 365 users and servers with spammers, Crypto Locker schemes, malware, viruses, and, in some cases, outright threats. The ways in which they infiltrate people’s email accounts has become more and more sophisticated as well, and Office 365’s low-grade spam filters have made these sorts of malicious behaviors easier and more effective.
Luckily, as these attacks become more prevalent, the solutions do as well. Cyber security companies like Securence have developed custom email protection packages that help keep your emails safe from attacks and other inconveniences that come with Office 365 services. Securence can help your Office 365 users stay safe while staying connected. Here’s how.
Simple, Affordable Filtering
Securence’s email filtering services have Zero Minute update technology providing the most effective blocking signatures in the industry, which will help keep your inboxes free of toxic email scams, spam, and phishing schemes. Best of all, it can be done for as little as a dollar a month.
Securence’s email filtering services are constantly updated with new security protocols, which can help keep your inboxes free of toxic email scams, spam, and phishing schemes. Best of all, it can be done for as little as a dollar a month.
Disaster Recovery
No matter how well you filter emails, disaster may still come. It could be the result of a virus or malware sent through an email that bypassed security. It could be because Office 365 has had to shut down its servers from time to time for maintenance and security reasons.
When your email goes down in today’s world, your business can come to a screeching halt. With disaster recovery options, however, you can gain uninhibited access to your emails, no matter the state of Office 365’s servers. Securence’s disaster recovery protocols keep backups of all your user’s emails on a separate server. In the event of a server issue at Office 365, your users will still be able to access, send, and receive emails. When the original servers are back up and working, the new emails and activity will be automatically updated, letting you enjoy seamless email access and communication, no matter the state of the original servers.
Microsoft’s Office 365 offers some of the most widely-used and powerful programs that are available to modern businesses. Each of the applications has become the standard for the office world almost anywhere on the globe. That prevalence, however, comes with a few risks, and Office 365 users can be targeted by multiple malicious attacks. That is why every Windows product should have its security bolstered, and Securence has effective, affordable services that can help. With email filtering services and backup protocols, you can enjoy seamless email service that’s also more secure, keeping you and your Office 365 users safe and connected at the same time.
Office 365 Securence Security Suite = Peace of Mind
Microsoft’s Office 365 is the absolute gold standard of office programs; it’s a powerful suite that offers almost everything the modern business needs. But even with its stellar programming, Office 365 lacks in some key areas, especially security for email. Enter Securence’s Office 365 Security Suite, a convenient and powerful service that will keep you more connected in the event of server failures, all while providing the latest in protection from everything from malware to spam.
Securence’s Office 365 Security Suite offers a broad scope of security protocols and services that complement your company’s security needs. Here are just a few of its most powerful features.
 1. Email Shadowing
1. Email Shadowing
Sometimes, Office 365 loses information. The reasons can be complex or simple, but it doesn’t really matter because the end result is the same: you could stand to lose important emails and communications whenever Office 365 goes down, which it occasionally does. Securence’s Office 365 Security Suite includes 30 days of instant email recovery of any inbound or outbound message, a service even Microsoft cannot provide. That way, you can recover and follow up on those important messages as you need to, not when Office 365 is able to do so.
2. Email Continuity
Email depends on servers, and servers, unfortunately, go down, crash, need maintenance, and, in some cases, lose vital information. Securence’s email shadowing protocols create a total, and totally safe, copy of your emails so that, when the servers go down, you can experience seamless email use that will then upload the new information onto your original servers once they are back online.
3. Powerful Antivirus Software
Securence’s Office 365 Security Suite offers 17 layers of antivirus, phishing, and spam blocking protection, keeping your inboxes and outboxes safe from the spread of malicious malware and scams that frequent unprotected email accounts. With such powerful protection protocols, our antivirus keeps you safe with the lowest false positive system ever invented, meaning less unwanted emails get through while every bit of information is still scanned for its safety.
4. An Easy-to-Use Outbound Smart Host
Our Office 365 Security Suite includes admin and user notifications, an easy release system, and a dedicated IP address. This will help your company stay out of blacklists that have become an issue for many Microsoft users because the company’s shared pool includes companies with bad sending practices. With our own system dedicated to your company, you will experience more efficient and more effective email, all while receiving important notifications about the status of your email service.
Microsoft’s Office 365 is the gold standard of office products, yet it still needs some extra help in key areas of its application, especially when it comes to email security. Securence’s Office 365 Security Suite delivers this much-needed security with a complex set of security measures that will keep your information safe while offering a continual connection to the digital world. If your company loves Office 365 but requires more security, contact Securence to discuss how you can run a safer, more connected company.
Quarantine and Digest Updates
Significant changes are being made to the Quarantine and Digest services. The changes include many formatting improvements and new features. We will gradually be upgrading all accounts to receive these improvements over the next 4-6 weeks.
The changes have been aimed at streamlining the most commonly used functions and we believe it will make your interactions with these services less cumbersome and more efficient. We hope you’ll agree! Let us know by dropping a note to support@securence.com.
New features:
- Allow – If you have access to your trusted senders (whitelist), you will now see an Allow action link next to each message in your digest. This will deliver the message to your inbox and add the sender to your list of trusted senders, to prevent future blocks. The message will also no longer appear in the quarantine (no need to delete it separately).
- Block – If you have access to your blocked senders (blacklist), you will now see a Block action link next to each message in your digest. This removes the message from your quarantine and drops future messages from that sender by adding their address to your personal blacklist. You will no longer see messages in your quarantine or digest if you have chosen to block them.
Changed features:
- Release – As before, this will deliver the message to your inbox. Now, by default, it also removes it from your quarantine view (no need to delete it separately).
- Report False Positive – This option has been removed since it is no longer necessary. Securence’s machine learning algorithms take all released and allowed messages into consideration when analyzing for inaccurate signatures. By releasing or allowing a message, you are indicating to Securence that it is not spam.
Further details for administrators:
- User-level quarantine and digests now filter out released messages by default. Released messages may be viewed by using the Advanced Search options in the quarantine. (“Allowing” a message also releases it, so those are filtered out by default as well)
- As indicated above, messages matching user-level blacklists will no longer appear in the user’s digest or quarantine. However, they will still be visible in the domain-level quarantine for help desk support.
- To simplify and improve mobile viewing, two columns have been removed from the digest: To and Type. The list of affected To addresses is now included at the bottom of the digest.
- The date column has been replaced with a time column. Messages are still sorted by datetime with most recent first. Therefore, messages on the same date are grouped together with a date header.
- The digest has an improved appearance in MS Outlook and on mobile devices.
- The “From” column of the digests now displays the sender address found in the RFC5322.From header. Previously, the RFC5321.MailFrom (envelope sender) was displayed.
- If you are eager to try out these new features on your domain, please let us know by e-mailing support@securence.com. Otherwise, look for these changes to be applied to your domain within the next month or so.
What is Encrypted Email?
Email encryption is one of those topics that gets very complicated very quickly. Pretty soon, most explanations end up using a bevy of complicated words and terms that may as well be another language. It doesn’t have to be this way, however, because the benefits of using encrypted email are simple, and the core concepts of email encryption can be easy to understand as well. Today, we decided to break down email encryption to its basics so you can learn what email encryption is and why it’s important for your business, without all the technical mumbo jumbo.
1. What is Email Encryption?
Email encryption is a way to protect your emails from being read by other people or computers. Essentially, what it does is scrambles an email heading out from your computer and reassembles it for the intended person. And when you receive an email, it scrambles it and puts it back together again before you read it, reducing the chances of any of the information getting into the wrong hands. By using encrypted email, the only people who will see an email is the sender and its intended recipients.
2. Why Do People & Companies Use Encrypted Email
Like most technological services, email encryption is used for a number of reasons. The overarching reasons, however, boil down to security and privacy. In general, companies use email encryption to meet security protocols. Since sensitive information is often sent through email, it is important for businesses to keep that information as protected as possible.
 Privacy is the other major reason, and this is often why individuals will use email encryption for their own private email accounts. Since the online experience increasingly uses software to track the movements of people online, emails are becoming easier and easier to break into or spy on. With email encryption, those emails can travel more safely and can better maintain their privacy.
Privacy is the other major reason, and this is often why individuals will use email encryption for their own private email accounts. Since the online experience increasingly uses software to track the movements of people online, emails are becoming easier and easier to break into or spy on. With email encryption, those emails can travel more safely and can better maintain their privacy.
3. Do I Need Email Encryption?
Generally, email encryption is recommended for two reasons: because your email always has sensitive information, and because you should be compliant with security protocols.
First off, your email account has private information. Everything from emails about resetting passwords to notices from you bank include information that could compromise your confidentiality. So even when you think your email is mostly for confirming appointments and seeing who’s having a sale this week, they are actually loaded with stuff you want to keep to yourself.
Secondly, if you run a business that has clients, you should be taking steps to ensure any information sent between your two parties is confidential. This includes using encrypted email to help keep things secure.
Encrypted email is absolutely essential in the modern business world, but that doesn’t mean it needs to be complicated. The technology itself may be quite fascinating, but the benefits are immediate: with encrypted email, you will be safer, your company’s information will be safer, and you will enjoy a level of privacy previously unavailable through unencrypted email. Don’t take chances when it comes to email encryption, contact Securence today to see what we have to offer.
Why You Should Send Encrypted Emails
It goes without saying that email is an essential aspect of the modern business. No longer a helpful tool, it has become integral to how companies and people communicate, both internally and externally. Being as essential as it is, keeping your emails safe from prying eyes, and keeping your information protected, is also key to running your business, no matter the size or industry.
Email encryption services can help your company succeed, save money, and stay compliant with business standards and protocols. Here are just a few reasons why you need to send encrypted emails.
1. Client Confidentiality
In a world that is increasingly connected, privacy and confidentiality have become extremely important. For many modern businesses, especially business-to-business companies, having up-to-date security is integral to your business and its clients.
Encrypted email is just one of the ways you can help ensure your company has the right security protocols in place to protect your company, and your clients, from data breaches.
2. Increased Security
Imagine the following scenario: your website is hit with a DDoS attack, halting traffic heading to your website. In order to fix the problem, you request a password change for your server. That is sent to you through an unencrypted email, meaning that anyone looking at your inbox has access to that password, and now the backend of your entire website. Not only is your site compromised, but all of its data is in the hands of someone else. At best, this is an extreme liability; at its worst, the people who visit your site are now vulnerable, all because of a single email containing a critical password.
 Email encryption helps to protect your company from these sorts of events, which can occur through a number of unintentional and intentional communications. Without the right protections, even a simple password reset email can end up as a far worse situation.
Email encryption helps to protect your company from these sorts of events, which can occur through a number of unintentional and intentional communications. Without the right protections, even a simple password reset email can end up as a far worse situation.
3. Secure Financial Transactions
We often think of inboxes as filled with communications and, as a result, tend to overlook just how much information is stored in those communications. We also tend to forget that things like bank transfers happen through our email accounts, and those can often be tied directly to our bank accounts. Regular, insecure email accounts leave you and your company open to people who are spying on and possibly stealing money and information related to your finances, and that can cause severe problems for your company’s longevity and ability to remain financially stable. But encrypted emails can help stop people from learning your financial dealings through your communications, and thus can keep your company protected.
With our modern dependency on email, it is extra important that you take all of the steps necessary to ensure that this email is protected. After all, important and confidential information is transferred through email every day, and it is your responsibility to ensure that it is away from prying eyes.
If you are in the need for email encryption services, Securence can help. With our email encryption technology, we can provide the maximum security for your most sensitive email communications and protect your business.